Continuing with the security enhancements, in this second part we will see about vSphere Trust Authority
vSphere Trust Authority secures a vSphere environment and its workloads:
• Uses a hardware root of trust to secure the environment
• Reports on the software running on a host
• Measures or attests software using a Trusted Platform Module (TPM)
A Trust Authority administrator must configure the following parameters:
• Permitted versions of ESXi
• Trusted TPM manufacturers or devices
A trusted key provider is required. A valid attestation report is needed before access is granted to the key provider.
Use Case for vSphere Trust Authority
We can use vSphere Trust Authority to perform security tasks:
• Provide ESXi hosts with a hardware root of trust and remote attestation capabilities.
• Perform cryptographic operations on VMs with an enhanced level of encryption key management.
• Restrict encryption key management by releasing keys only to attested ESXi hosts.
In vSphere 7, we can create a trusted computing base, which consists of a secure, manageable set of ESXi hosts. vSphere Trust Authority implements a remote attestation service for the ESXi hosts that we want to trust.
Furthermore, vSphere Trust Authority improves on Trusted Platform Module (TPM) 2.0 attestation support (added to vSphere beginning in the 6.7 release). vSphere Trust Authority implements access restrictions on encryption keys and better protects VM workload secrets. In addition, vSphere Trust Authority allows only authorized Trust Authority administrators to configure vSphere Trust Authority services and hosts. The Trust Authority administrator can be the same user as the vSphere administrator user, or a separate user.
vSphere Trust Authority
vSphere Trust Authority improves on encryption and attestation:
• We require attestation for key access.
• vSphere Trust Authority uses a hardware root of trust.
• Key handoff is through the vSphere Trust Authority Cluster.
• We can encrypt vCenter Server when using vSphere Trust Authority
In vSphere 6.x, VM encryption and attestation work in the following ways:
• Attestation is a read-only view, and no repercussions occur when it fails.
• The attester is vCenter Server.
• Key handoff occurs through vCenter.
• We cannot safely encrypt vCenter because it forms a dependency on key access.
vSphere Trust Authority Components
vSphere Trust Authority comprises a Trust Authority Cluster and a trusted key provider. Other ESXi clusters are attested against the Trust Authority Cluster.

Several concepts apply to vSphere Trust Authority:
• The vSphere Trust Authority Cluster is a set of restricted ESXi hosts with a known good configuration.
• vSphere Trust Authority is administered by a small number of trusted administrators.
• The trusted key provider (also called key management server, or KMS) is a key provider that only the Trust Authority Cluster should know.
• The attested cluster is the Trusted Cluster. The attestation report for a cluster must be validated by the Trust Authority Cluster.
About vSphere Trust Authority Administrator
To enable vSphere Trust Authority, you must add a user to the vSphere TrustedAdmins group:
• This user becomes the Trust Authority administrator.
• We use a separate user from the vCenter Server administrator as your vSphere Trust Authority administrator.
• We must add a Trust Authority administrator for both the Trust Authority Cluster and the Trusted Cluster.
• Group membership is validated by ESXi using SAML token authentication.
ESXi Components
New services run on ESXi enabled with vSphere Trust Authority:
• Attestation Service (attestd)
• Key Provider Service (kmxd)
• Trusted infrastructure agent (kmxa)
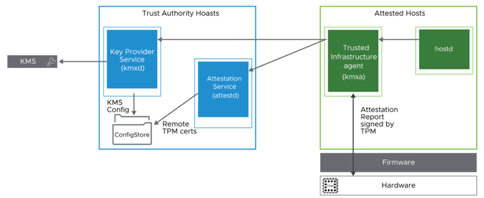
Attestation Service
The Attestation Service on the ESXi host verifies the remote software and hardware:
• Receives an attestation report from the trusted infrastructure agent of the attesting ESXi hosts
• Verifies that a TPM device is present on the attesting ESXi hosts
• Verifies the ESXi version of the attesting ESXi hosts
• Generates a signed document describing the binary and configuration state of the attesting ESXi hosts
A Trust Authority administrator must configure:
• Which versions of ESXi to trust
• Which TPM device manufacturers to trust
• (Optional) Which specific TPM devices to trust
The Attestation Service performs the following functions:
• Generates a signed document that contains assertions describing the binary and configuration state of the remote ESXi hosts in the Trusted Cluster.
• Attests the state of the ESXi hosts using a Trusted Platform Module (TPM) 2.0 chip for software measurement and reporting. The TPM measures the software stack and configuration data and reports it to the Attestation service.
• Verifies that the software measurement signature can be attributed to a previously configured trusted TPM endorsement key (EK).
• Ensures that the software measurement matches one of a set of previously compliant ESXi images.
• Signs a SAML token that it issues to the ESXi host, providing the assertions about the identity, validity, and configuration of the ESXi host.
Key Provider Service
For the Key Provider Service to connect to a key provider, you must create a trusted key provider, configure a trust setup between the Trust Authority Cluster and the KMS.
The Key Provider Service (kmxd) provides a method for encapsulating encryption key sources:
• The service supports KMIP-compliant key servers.
• Additional protocols can be added in the future.
• The service allows encryption key access only if a client presents a valid attestation report.
With the Key Provider Service, vCenter Server and ESXi hosts do not require direct key management server (KMS) credentials. In vSphere Trust Authority, an ESXi host can access an encryption key by authenticating with the Key Provider Service rather than with vCenter Server (as in vSphere 6.7).
For the Key Provider Service to connect to a KMS, the Trust Authority administrator must configure a trust setup. For most servers that are compliant with the Key Management Interoperability Protocol (KMIP), we configure a trust setup by creating client and server certificates.
Trusted Infrastructure Agent
The trusted infrastructure agent (kmxa) communicates with a trusted Key Provider Service and Attestation Service:
• The trusted infrastructure agent retrieves encryption keys from the trusted Key Provider Service.
• The agent can be issued with encryption keys only if the ESXi host passes attestation.
• The ESXi host does not receive encryption keys from vCenter Server when the host uses a trusted key provider.
Ports Used by vSphere Trust Authority
All vSphere Trust Authority services run behind the reverse proxy and API forwarder. The trusted infrastructure agent communicates over port 443 to the vSphere Trust Authority hosts.
The following internal ports are used:
• Attestation Service: Port 7889
• Key Provider Service: Port 7888
• Trusted infrastructure agent: Port 7890
vCenter Server Topologies
vSphere Trust Authority requires two or more vCenter Server systems. The Trust Authority Cluster must reside in a different vCenter Server inventory than the Trusted (attested) Cluster but can participate in Enhanced Linked Mode.
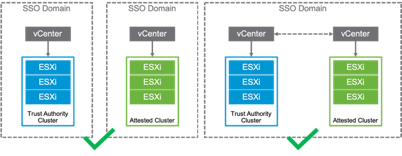
A single vCenter Server instance that manages both the Trust Authority Cluster and the Trusted (attested) Cluster is not supported.

vSphere Trust Authority Workflow
In the vSphere Trust Authority workflow, a Trust Authority administrator performs the following tasks:
1. Exports the identity of the hosts to be attested
2. Enables trusted host services on a Trust Authority Cluster
3. Imports the identity of the attesting hosts into the Trust Authority Cluster
4. Configures a trusted key provider
5. Exports the identity of the Trust Authority Cluster
6. Imports the Trust Authority Cluster identity into the attesting cluster
7. Configures the Trust Authority Cluster as the key provider for the attesting cluster
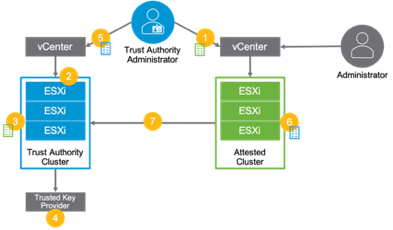
Enabling vSphere Trust Authority
In vSphere 7, we enable vSphere Trust Authority primarily through PowerCLI:
• PowerCLI 12.0 provides a new set of PowerCLI cmdlets.
• To run the PowerCLI cmdlets, you must be a member of the TrustedAdmins single sign-on group.
VM Encryption with vSphere Trust Authority
The user experience of VM encryption does not change when it is used with vSphere Trust Authority in vSphere 7:
• We can encrypt a VM by applying an encryption storage policy.
• When we add a virtual TPM device to a VM, the VM is encrypted.
• An attested cluster uses a trusted key provider.
• We can use a mix of a trusted key provider and a standard key provider in the same vSphere environment.
Identifying VM Encryption Key Providers
In the vSphere Client, the VM summary indicates the type of key provider that is used for encryption. A VM that is encrypted with a trusted key provider has a slightly different icon from a VM encrypted with a standard key provider.
The crypto-util dictionary describe /path/vm.vmx does not indicate whether the VM is encrypted with a standard or trusted key provider. However, the key provider name is present in the output so you can determine the key provider type.
A VM encrypted with a standard key provider can be migrated to an attested ESXi host, but it continues to use the standard key provider.
Migrating a VM Encrypted with a Trusted Key Provider
A VM that is encrypted with a trusted key provider cannot be migrated to an ESXi host that is not attested against the same vSphere Trust Authority Cluster.
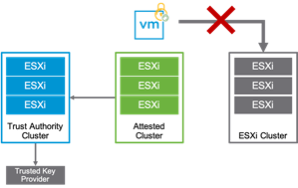
In the vSphere Client, a compatibility issue indicates that the destination host is not trusted and attested.

Closing Note
I hope it has been useful to you. See you next!

