To create and modify virtual machines in vSphere, we must understand the VM settings and features that are available. vSphere 7 introduces a new ESXi compatibility version that adds new virtual devices and features that you can use to enhance the functionality of VMs.
VM Compatibility Version
vSphere 7 introduces the VM compatibility level for ESXi 7.0 and later, adding new functionalities:
• New EVC modes for additional processors
• Virtual SGX for runtime protection of the VM
• A virtual watchdog timer (WDT) to assist clustering software that implements heartbeats
• Selective latency sensitivity
• A precision clock to improve timekeeping in the guest OS
The VM compatibility level for ESXi 7.0 and later also adds support for new devices:
• Local NVMe devices
• USB 3.1 devices
• PCIe storage device hot-plug support
vSphere 7 introduces hardware version 17, which provides native instruction support for the Intel Cascade Lake and AMD Rome processors.
About Virtual Watchdog Timer
The virtual WDT detects and recovers from OS problems. If a failure occurs, the WDT attempts to reset or power off the VM.
This feature is based on Microsoft specifications: Watchdog Resource Table (WDRT) and Watchdog Action Table (WDAT).
The WDT is a virtual device that detects and recovers from OS problems. The device’s timeout can be initialized with VM power-on, or by the guest OS. The guest OS or an application in the guest OS can reset the device’s timeout based on a predefined logic. If the virtual WDT is not reset before its timeout, it resets or powers off the guest OS.
How the guest OS or the application in the guest OS interacts with the virtual WDT differs depending on the guest OS and the application that interacts with the virtual device.
Virtual Watchdog Timer Use Cases
The virtual WDT is useful in the following scenarios:
• With high availability solutions such as Red Hat High Availability and the MS SQL failover cluster
• On VMware Cloud and in hosted environments for implementing custom failover logic to reset or power off VMs
Many high availability solutions require watchdog devices. These high availability solutions can use the virtual WDT. The timer’s use in high availability solutions might differ from one vendor to another.
The Red Hat High Availability Add-On is a clustered system that provides reliability, scalability, and availability to critical production services. RHEL HA uses watchdog devices in their clustering solution. It supports watchdog timer devices (hardware devices) and virtualization-emulated watchdogs (virtual devices). RHEL HA does not support software-emulated watchdogs. With the introduction of the virtual WDT, RHEL HA clusters can be created on the vSphere infrastructure.
Using the virtual WDT, users can implement their own failover logic to reset or restart a VM.
Virtual Watchdog Timer Requirements
We must meet the following requirements for the virtual WDT:
• VM must include hardware version 17 or above.
• VM must be powered off before adding the virtual WDT.
• Guest OS support must be provided for the watchdog timer:
— Windows Server 2003 (WDRT)
— Windows Server 2008 onward (WDAT)
— Linux (kernel version 4.9 or above)
Other guest operating systems, such as FreeBSD, MAC OS X, are not supported. For Linux operating systems with kernel 4.9+, verify that the module wdat_wdt.ko is installed. No additional drivers are required in Windows and the Linux OS. Linux support for Windows Server 2003 (WDRT) is no longer available.
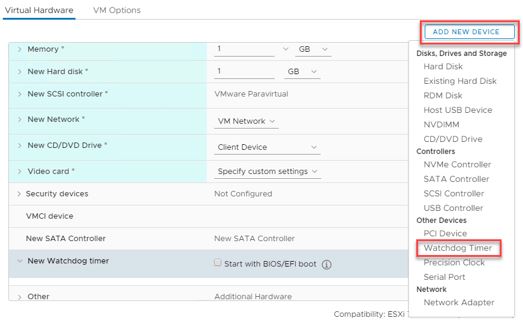
Adding Virtual Watchdog Timer to a VM
We can use the vSphere Client to add the virtual WDT to a VM
About SGX
Intel Software Guard Extensions (SGX) technology meets the needs of the trusted computing industry:
• With Intel SGX, software programs can create private memory regions called enclaves.
• Data in enclaves can be accessed only by the intended program.
• The enclave region is isolated from other programs, operating systems, hypervisors, and so on.
• Enclaves are used by the software program to secure data.
• Virtual SGX exposes Intel’s SGX to VMs running in a vSphere environment.
Trusted computing refers to various technologies and proposals for resolving computer security problems. The problems are resolved through hardware enhancements and associated software modifications. Data inside an application can be compromised by rogue software or a bug in the operating system or in the hypervisor. Programmers can use Intel SGX to create private memory regions called enclaves. Data in enclaves is protected from unauthorized access and modification by rogue software running at higher privilege levels. Intel SGX provides this protection without disrupting the ability of legitimate software to schedule and manage the use of platform resources. Virtual SGX is implemented as part of the vSphere core virtualization stack. With virtual SGX, applications running on VMs can create their own enclaves.
SGX Terminology
Enclave Page Cache (EPC) is a static portion in RAM that is used for storing running enclaves. The launch control configuration determines which enclaves can be started. Enclave Page Cache (EPC) is a static portion of physical RAM. This portion is allocated at boot time by the BIOS. EPC stores running enclaves. EPC is a limited resource, typically not more than 93 MB. The launch control configuration is an architectural component from which the platform can control the enclaves to be started.
Virtual SGX Use Cases
We can use virtual SGX in several scenarios:
• For applications such as secure remote computing, secure web browsing, and digital rights management
• For VMware virtual appliance components
• For applications that must conceal proprietary algorithms and encryption keys
• Where you do not want cloud service providers to inspect the client’s code and data
Many third-party applications can use virtual SGX.
Intel SGX Architecture
SGX reduce the attack surface of a malicious application

Applications frequently work with private information such as passwords, encryption keys, bank account numbers, and so on. This private data should be accessed only by the designated recipient. The job of the operating system is to protect such private data from other applications and users. Operating systems and applications often employ safeguards to protect this private data. Despite these protections, most computer systems are still vulnerable. Malware with administrative privileges can access all operating system resources, including all applications running on that system. Malware can target an application’s protected data to extract encryption keys and secret data directly from memory. With Intel SGX, applications can create enclaves, which protect the confidentiality and integrity of applications from privileged malware. Privileged malware is malware that gets privileges by manipulating the underlying system.
Virtual SGX Requirements
To use virtual SGX, you must meet the following requirements:
• The ESXi host must have Intel Coffee Lake CPUs or later.
• SGX must be enabled in the BIOS of the ESXi host.
• Hyperthreading must be disabled on certain Coffee Lake SKUs.
• Virtual hardware version 17 or later is required.
• VMs must be powered off.
• Supported guest operating systems are:
— Windows 10
— Windows Server 2016 or above
— Linux
All versions of Linux with the required kernel and modules are supported. A special kernel module published by Intel must be loaded. This kernel module is available for only some Linux distributions.
Virtual SGX Restrictions
Virtual SGX has the following restrictions:
• For VMs configured with virtual SGX, the following operations are not supported:
— Live migration with vSphere
— Suspend and resume
— Snapshots
— Fault tolerance
• For virtual SGX enabled VMs, the following VM configuration attributes are fixed:
— Guest firmware type: EFI.
— Standby response: Put the guest OS in standby mode and leave the VM powered on.
Cold migrations can be performed.
Enabling and Disabling Virtual SGX for a VM
In the vSphere Client, we can enable or disable virtual SGX on the Virtual Hardware tab under Security devices.

We can use the Edit Settings menu to enable and disable virtual SGX for a VM. The VM must be powered off to enable or disable the feature.
Guest Customization Improvements
vSphere 7 includes new REST APIs for guest customization:
• Create, Update, Set, Delete spec
• List, Get, Apply spec
• Import/Export spec to/from JSON
We can now create pre-and post-customization scripts in our preferred scripting language (sh, bash, Python, and so on). With the new REST APIs, we can interact with guest customization outside of the vSphere Client.
About Precision Clock
vSphere 7 introduces a virtual device called Precision Clock:
• The guest OS uses the Precision Clock time as reference time.
• Precision Clock is not directly involved in guest OS time synchronization.
• Precision Clock presents the ESXi host’s system time to the guest OS.
• To provide better time synchronization, Precision Clock bypasses the virtual networking stack and the guest networking stack.
• Precision Clock helps the guest OS to achieve clock accuracy in a 1 millisecond range.
VMware Tools provides a plug-in called Tools TimeSync. This plug-in synchronizes VM time with ESXi time. This tool is not recommended over guest native agents such as ntpd, chrony, and W32Time.
Precision Clock Use Cases
Precise timekeeping is a requirement for many applications, for example, financial services applications. Precise time stamps are required on events that track financial transactions. Precision Clock helps ensure that the guest OS is accurate and that the applications running in the guest have accurate timestamps. In financial services applications, the time stamps on transactions and records must be precise. The financial sector must adhere to many regulations to time-stamp records and transactions. These time stamps must be accurate within a 1 second range.
Precision Clock Requirements
Precision Clock requires ESXi compatibility level for ESXi 7.0. Other requirements include:
• Precision Clock is available only for Linux guests.
• On Linux VMs, only the chrony time sync tool is supported.
• The Linux guest must have the vmwptp driver installed.
• The ESXi host must be synchronized with either the Network Time Protocol (NTP) or the Precision Time Protocol (PTP).
Adding and Configuring Precision Clock
We add and configure Precision Clock using the vSphere Client

Precision Clock has the following optional device settings:
• Host system time (Auto): Precision Clock automatically detects the ESXi host’s time-sync protocol and presents the time to the guest OS.
• Host system time (NTP): Precision Clock requires that the ESXi host’s time-sync protocol is the Network Time Protocol (NTP).
• Host system time (PTP): Precision Clock requires that the ESXi host’s time-sync protocol is the Precision Time Protocol (PTP).
For more information about how to set up NTP on the ESXi host, see VMware knowledge base article 57147
Migration of VMs with Remote Devices
In vSphere 7, we can migrate a VM with a device attached through a remote console.
Requirements for this feature are:
• vCenter Server 7.0
• ESXi 7.0
• VMware Remote Console with reconnect support
Previously, we could not use vSphere vMotion to migrate a VM with a floppy or CD-ROM device attached through a remote console (VMware Remote Console, Workstation, Workstation Player, and Fusion). These remote devices might be physical devices or on disk images on the client machine running a remote console. This limitation causes issues when we try to evacuate all VMs from a host to reduce the time for performing host upgrades. Earlier versions of VMware Remote Console, vSphere, and ESXi do not support migration of VMs with remote floppies or CD-ROMs.
Virtual Machine Maximus for Large Workloads
With the introduction of VM compatibility level for ESXi 7.0 in vSphere 7, the CPU and RAM limits per VM are increased. A VM running a compatibility version of ESXi 7.0 supports:
• 768 vCPUs
• 24 TB of RAM
When using vSphere vMotion to perform a migration of a large VM, we should have 40 Gb links on the vSphere vMotion network.
About Instant Clone Guest Customization
With instant clone guest customization, we can modify the network settings of a running VM:
• Customization is done without powering off or restarting the VM.
• This customization feature is only available for Linux VMs.
• Instant clone guest customization is an API-only feature.
We can customize networking settings such as IP address, DNS server, and gateway. We can change these settings without powering off or restarting the VM.
Instant Clone Guest Customization Use Case
We can use the instant clone guest customization in various ways:
• Customize network settings of an instant clone.
• Customize network settings of a normal running VM.
Instant Clone Guest Customization Requirements
To use instant clone guest customization, we must meet several requirements:
• The customization engine must be installed on the guest OS.
• The feature is supported only for Linux VMs.
• Version restrictions:
— vCenter version 7.0 or later.
— ESXi version 6.0 or later.
— VMware Tools version 10.2 or later.
Closing Note
I hope it has been useful to you. In a future Blog, we will see a Storage Enhancements. Thanks!

